Be
More
Productive
Our priority at Seifert Companies is ensuring your success. Whether you’re seeking to expand your manufacturing capabilities with new machines and automation, increase your technological performance, or enhance your workforce, we’re here to ensure that the process is well-planned and executed.
Our team of mechanical and electrical engineers, network engineers and programmers, in Ohio and Tennessee, are experienced in a wide variety of business processes, ensuring you will be more productive.

"The staff at Seifert Technologies demonstrated an outstanding ability to grasp our issues and work effectively with us to solve our most difficult challenges. It is so refreshing to receive a prompt and professional service."
- Rick Bednar, CEO - TenPoint Crossbow Technologies Company
Button
"Your candidates were consistently among the best prepared and strongest candidates we interviewed."
- HR Manager - Canton, OH Manufacturing Company
Button
"Not only are you great engineers, you are also great collaborators! You have been extremely helpful by delivering an amazing service and an astonishing final product! Your work is excellent and I couldn't be happier with it! I look forward to working with you again."
- Project Engineer - NFM Welding Engineers
Button
"I am quite impressed by Seifert’s diligence in proactively identifying the problem and the speed and skill with which they addressed the challenge so as to avoid disruption to our business. I can’t say enough good things about how this project has been handled. Great Job!"
- Peter Martin - Tower Industries
Button
“The knowledge and professionalism are nothing short of stellar. We would be spending significantly more time and money without the design assistance we receive from Seifert.”
- Eric Hickenbottom - Die Shop Supervisor - Meteor Sealing Systems
Button
Seifert Companies Blog

By Seifert Engineering
•
November 26, 2025
Upgrading or expanding an existing facility is one of the most complex challenges manufacturers face. Every project must fit seamlessly into a real-world environment that’s often full of legacy equipment, tight clearances and unknown obstacles. And when it comes time to expand or modernize a facility, gaps in documentation can make even a straightforward project feel like a maze. Even small inaccuracies in as-built drawings can create costly delays, rework or mismatched designs. That’s why more manufacturers are turning to point cloud–driven design —a workflow that turns real-world spaces into precise digital environments. Point clouds give teams a clear, accurate picture of what they’re working with—no guesswork, no faded blueprints, no surprises tucked behind a support column. At Seifert Engineering, we use point cloud data to help customers plan smarter expansions, design workflows with confidence, and move projects forward without the usual headaches that come with upgrading older spaces. What Makes Point Clouds So Useful? A point cloud starts with a 3D laser or LiDAR scan. The scanner fires out millions of measurement points, each one recording an exact X-Y-Z location. This creates a highly accurate digital representation of the facility as it exists at that moment—equipment, walls, mezzanines, conduit, pipe runs… everything. For manufacturers, this precision directly translates into better outcomes. Teams can: Measure from the digital model instead of making repeated site visits Identify potential interferences before fabrication Plan equipment layouts more efficiently Build new designs that fit right the first time It’s a way of turning a complex physical space into something engineers and decision makers can use to explore, measure and design within—all from the comfort of their desks. From Scan to Smart, Usable Data After a scan is collected, the raw data moves through specialized processing tools that help clean it up, aligning geometry and removing noise and irrelevant details. Multiple scan sets can be merged when a project covers large or segmented areas. Once prepared, the point cloud is exported to a format that works easily with modern CAD environments. From there, it becomes the foundation for future designs—essentially a digital “as-built” model that informs every decision that follows. This processing step is one of the biggest reasons point clouds are so powerful. Instead of trying to interpret messy or incomplete data, engineers work from a clean, reliable model that mirrors the real facility inch by inch. Designing Inside the Real Environment The moment a point cloud is loaded into CAD, things get interesting. Instead of designing equipment or platforms in a blank workspace, engineers can build directly inside the scanned environment. It's the difference between designing a staircase using a generic wall height… and designing one that you know clears that pipe rack by exactly 2.37 inches. Working this way makes projects move faster and reduces the friction that normally comes with upgrading older spaces. You can: Check clearances instantly Validate equipment fits before fabrication Build geometry that aligns with existing structures Catch conflicts while the design is still flexible And because the model is visual and intuitive, approvals tend to move faster. Stakeholders can “see” the project long before installation day. Better Planning, Better Workflow, Better Results Whether you’re relocating a fabrication line, adding automation or expanding a production area, point cloud–driven design gives you the clarity needed to plan effectively. Teams can test different layouts, compare workflows and evaluate how new equipment changes material movement or operator access. It also reduces two major project stressors: rework and downtime. When the model reflects reality, you’re far less likely to discover an unexpected beam, conduit run or floor variation during installation. That accuracy means fewer on-the-fly adjustments—and a much smoother upgrade process. A Flexible Tool for Any CAD Workflow Point cloud data integrates with most widely used design platforms, whether you're working in a mechanical, architectural or layout-focused environment. You don’t have to overhaul your entire workflow to use it; you can simply bring the point cloud in as a reference and design the way you always have—only now, you’re doing it with dramatically better information. For many manufacturers, that’s a breakthrough: point clouds elevate the quality of the design work without adding friction to the process. The Bottom Line Point cloud–driven design gives manufacturers a more accurate, reliable, and efficient way to plan facility upgrades. With a precise digital snapshot of the environment, teams can make confident decisions, reduce installation risk and design solutions that truly fit the space. At Seifert Engineering, we leverage point cloud data to help customers modernize with fewer surprises and better outcomes. Whether you’re preparing for an expansion, integrating new equipment or rethinking workflow efficiency, this approach creates a clearer path forward from day one. FAQs About Point Cloud–Driven Design What is a point cloud? A point cloud is a collection of millions of measurement points captured by a 3D laser or LiDAR scanner, each one marking an exact X-Y-Z coordinate. How accurate is point cloud data? Very. It provides a high-fidelity representation of the real environment, making it ideal for tight clearances, complex layouts and equipment integrations. Does point cloud data work with my CAD software? In most cases, yes. Point clouds can be imported into many modern CAD platforms using native tools or common plug-ins. Does this reduce site visits? Substantially. With a complete digital model, engineers usually only need one initial scan visit—everything else can be measured virtually. What types of projects benefit most? Facility expansions, new equipment installations, layout optimization, automation upgrades and any project involving tight spaces or unclear documentation

By Seifert Technologies
•
October 31, 2025
The cloud isn’t a trend anymore—it’s the foundation of modern IT. Yet, many businesses still hesitate to make the move. Maybe it’s uncertainty about cost, complexity, or security. Maybe your current systems “still work fine.” But as software, storage, and infrastructure continue shifting to the cloud, the real question becomes: is your business ready for the cloud—or are you being left behind? Cloud computing offers clear advantages: flexibility, scalability, resilience, and cost control. But successful cloud adoption requires more than flipping a switch. Without the right plan and preparation, companies can find themselves facing unexpected downtime, runaway costs, or security gaps that outweigh the benefits. Here’s a practical checklist to help you evaluate readiness, avoid common mistakes, and migrate with confidence. Step 1: Define the “Why” Before the “How” Before migrating a single workload, define your purpose. Are you moving to reduce infrastructure costs? Improve reliability? Support remote teams? Or modernize outdated systems? Your goals will guide every decision—what to migrate, how to structure it, and which provider fits best. Too often, businesses rush into the cloud because “it’s the direction everyone’s going,” only to discover they lack the use cases or ROI justification to sustain it long-term. Pro Tip: Create measurable success metrics before you start (e.g., reduce downtime by 30%, eliminate on-premises hardware by 2026). These benchmarks help you track progress and prove value later. Step 2: Audit What You Have Think of cloud migration like moving to a new house—you need to know what you’re packing, what to leave behind, and what needs upgrading. Start by cataloging your IT environment: servers, databases, applications, and network dependencies. Identify what’s cloud-ready versus what needs to be reworked. Some legacy systems may not play well in the cloud, while others can move easily with minimal changes. Don’t overlook data governance. Understand where your data resides, who owns it, and any compliance obligations (HIPAA, PCI, GDPR). These details determine how and where your data can be stored or transferred. Common Mistake: Skipping dependency mapping. Many migrations fail when teams move one system only to realize another critical app still points to an on-premises database. Step 3: Choose the Right Cloud Model and Strategy There’s no “one-size-fits-all” cloud. The right choice depends on your needs: Public Cloud (AWS, Azure, Google Cloud ): Scalable and cost-efficient, ideal for flexibility. Private Cloud: Better for sensitive workloads requiring full control and compliance. Hybrid Cloud: Combines both for balance—keep mission-critical systems on-premises while moving scalable workloads to the cloud. Also consider your migration strategy : Lift and Shift (Rehost): Move systems as-is to the cloud. Re-platform: Make light optimizations (like switching to managed databases). Refactor: Redesign for cloud-native architecture (ideal for long-term modernization). Choosing the wrong model can lead to inefficiencies or vendor lock-in later. Pro Tip: Start with a small pilot project to validate your strategy before scaling. Step 4: Plan the Move—Down to the Details Once your roadmap is clear, build a migration plan. This should outline: A phased migration schedule (by workload priority) Clear roles and responsibilities Communication plans for downtime or cutovers Security and access controls Backup and rollback strategies Testing is key. Always test workloads in a staging environment before flipping the switch. Common Mistake: Moving too much too soon. A phased approach reduces disruption and allows teams to learn as they go. Step 5: Prioritize Security and Cost Control Cloud security is a shared responsibility. Your provider secures the infrastructure—but you are responsible for access control, configurations, and data protection. Enable multi-factor authentication (MFA) , enforce strong password policies, and continuously monitor user access. Use encryption both in transit and at rest. And don’t forget to configure security groups and firewalls correctly—misconfigurations remain one of the top causes of cloud breaches. When it comes to cost, set up monitoring and alerts to track usage. Cloud services make it easy to overspend through underused resources or forgotten test environments. Pro Tip: Use your provider’s built-in cost management tools or a third-party platform to track usage trends and automate rightsizing recommendations. Step 6: Train Your Team and Build a Culture of Cloud Readiness Technology is only half of the equation—your people are the other half. Provide training to help IT staff understand new cloud tools, management consoles, and best practices. Encourage a culture of adaptability and continuous learning. For many organizations, working with a managed service provider (MSP) like Seifert Technologies can bridge the skills gap. A trusted partner can help your team transition smoothly while providing guidance on architecture, governance, and optimization. Step 7: Test, Optimize, and Evolve Migration isn’t a one-and-done event—it’s an ongoing journey. Once workloads are live, monitor performance, review KPIs, and identify opportunities to optimize. Cloud environments evolve quickly; what worked a year ago might not be cost-effective or secure today. Regularly revisit your cloud architecture to ensure it still aligns with business goals. Continuous improvement is what separates a successful cloud migration from one that simply “moved servers offsite.” Final Thoughts: Migration as Modernization Cloud migration isn’t just about moving data—it’s about modernizing how your business operates. When done strategically, it can improve performance, enhance security, and empower innovation across your organization. At Seifert Technologies , we help businesses modernize their IT environments with customized cloud migration strategies that minimize risk and maximize ROI. From readiness assessments to full-scale deployments, our team guides you every step of the way. Ready to see if your business is cloud-ready? Contact our team to schedule a Cloud Readiness Assessment and get your personalized migration roadmap. Call 330.833.2700 ext. 113 or email sales@seifert.com .
By Seifert Engineering
•
September 30, 2025
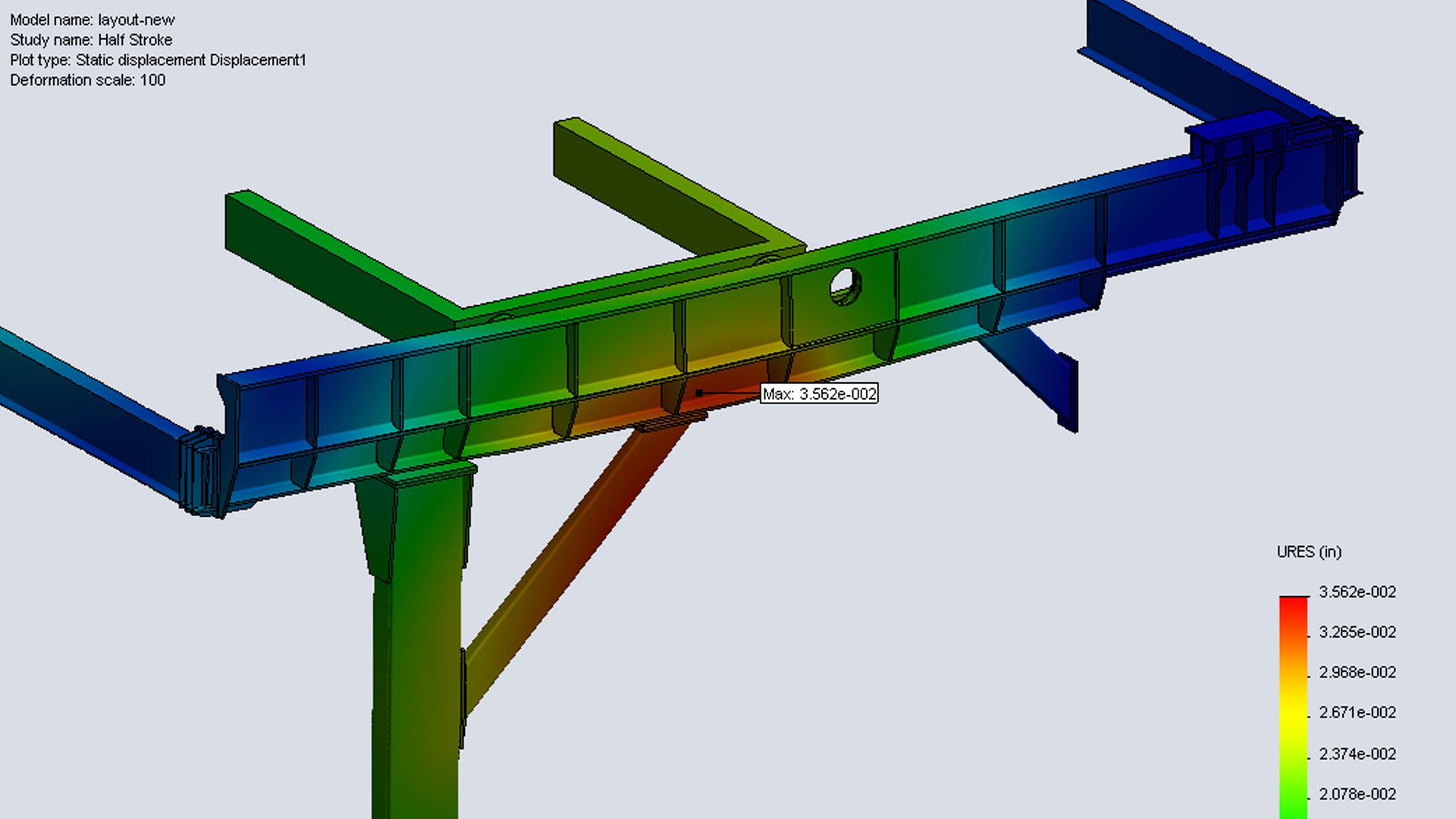
In today’s competitive marketplace, manufacturers are constantly challenged to do more with less—less weight, less material, and less cost—without sacrificing performance or safety. Welded assemblies are at the heart of countless products, from machine frames and robotic tooling to heavy-duty enclosures and transportation equipment. Each one must strike the right balance between strength, weight, and durability. That’s where Finite Element Analysis (FEA) comes in. At Seifert Engineering, we use FEA to help our customers create virtual prototypes of their weldments. This process allows us to simulate how an assembly will perform under real-world conditions, pinpoint stress concentrations, and explore redesign options before the first piece of steel is ever cut. The result? Lighter, stronger, and more efficient designs that save time and reduce costs. Traditional Weldment Design vs. FEA Optimization Traditionally, weldments have been designed with large safety factors. While this “better safe than sorry” approach works, it often leads to heavier structures than necessary. Extra weight increases material costs, makes handling and installation more difficult, and can even limit performance in applications where mobility or efficiency is critical. With FEA, engineers don’t need to rely on rules of thumb or oversizing. Instead, we can simulate exact conditions —stress, vibration, temperature, and more—to see how the weldment will behave. This digital stress test provides valuable insights into where material is truly needed for strength and where it can be safely reduced. Stress Risers in Weldments: What FEA Reveals One of the biggest advantages of FEA is its ability to reveal stress risers —the areas where failures are most likely to occur. In welded assemblies, these often include: Weld geometry and roots, where the shape changes dramatically. Connection points with bolts, pins, or fasteners. Transitions in material thickness , where loads aren’t evenly distributed. Corners and cutouts , which concentrate stresses. By identifying these critical zones early in the design process, we can reinforce them strategically while trimming away unnecessary weight in low-stress regions. FEA Meshing Strategies and Boundary Conditions for Weldments Running an FEA model isn’t just about clicking “analyze.” The quality of the results depends heavily on how the simulation is set up—particularly meshing and boundary conditions . Meshing strategies : The mesh is the network of small elements used to represent the weldment. Finer meshes in high-stress areas capture detail more accurately, while coarser meshes in low-stress areas speed up calculations. The right balance ensures reliable results without unnecessary computation time. Boundary conditions : These define how the assembly is constrained and loaded in the real world. Properly applying loads, supports, and connections is critical for making the simulation behave like the actual structure. At Seifert Engineering, our team’s experience ensures that each simulation is built on solid fundamentals, giving our customers confidence that the results will reflect reality. Visualizing Stress and Making Better Design Decisions One of the most powerful aspects of FEA is its ability to visualize stress concentrations through clear, color-coded plots. Instead of guessing, customers can literally see where their design is strongest and where it needs attention. These visual insights help guide collaborative conversations about redesign—whether that means adjusting weld sizes, changing materials, or redistributing loads. This process doesn’t just reduce weight and improve efficiency; it also builds confidence. Customers know that their design has been tested, validated, and optimized before fabrication begins. Partnering for Better Weldment Designs FEA is more than a software tool—it’s a way of thinking about design. At Seifert Engineering, we see it as an opportunity to partner with our customers . By combining simulation with our deep engineering expertise, we help companies bring better products to market faster, with fewer prototypes and lower development costs. Whether you’re working on a new weldment design or looking to improve an existing assembly, our team can help you optimize for strength, efficiency, and manufacturability. With FEA, you don’t have to choose between lightweight and durable—you can have both. 👉 Explore Seifert Engineering’s FEA services to see how simulation can support your next project. FAQs on Weldment Design and FEA Why use FEA for weldment design? FEA allows engineers to simulate stress and loading conditions, optimize material usage, and reduce weight without compromising strength. What are common stress risers in welded assemblies? Weld geometry, roots, fastener connections, material transitions, and cutouts are the most common areas where stress concentrates. Can FEA replace physical prototypes? Not entirely, but it significantly reduces the number of prototypes needed by identifying issues earlier in the design process.

By Seifert Technologies
•
August 29, 2025
“It won’t happen to us.” That’s what many business owners think—until it does. Ransomware has quickly become one of the most costly and disruptive threats facing businesses of all sizes. Unlike other cyberattacks, ransomware doesn’t just steal information—it locks you out of your own systems until a ransom is paid, often crippling operations for days or weeks. In June, we discussed how “ Data Backup Is Not Disaster Recovery .” Today, we’re taking that conversation further. Cybercriminals have grown adept at evading old defenses. Many ransomware attacks now target and encrypt backups first , leaving businesses with no safety net if they don’t have a full recovery strategy in place. So how can you prepare your business before it’s too late? The Evolution of Ransomware Ransomware has evolved from crude encryption schemes into complex, multi-stage attacks. The collapse of major groups like Lockbit and BlackCat has fractured the ecosystem, giving rise to lone operators and hybrid threat actors that blur the lines between cybercrime, espionage and hacktivism. New tactics include: Phantom scams : Fake ransom notes sent by mail Living Off the Land (LOTL) : Using legitimate tools to avoid detection Double extortion : Encrypting data and threatening to leak it Human-operated ransomware : Attacks rely on social engineering techniques and insider manipulation Real-World Impact of Ransomware Colonial Pipeline (2021): A ransomware attack shut down the largest fuel pipeline in the U.S. for nearly a week, causing fuel shortages and panic buying. City of Baltimore (2019): Attackers demanded $76,000 in ransom. The city refused—but ended up spending over $18 million recovering systems and services. Ingram Micro (2025): In July, IT distribution giant Ingram Micro suffered a global outage due to a ransomware attack by the SafePay group. The attack disrupted website access, order processing, and internal operations for nearly a week. Small Businesses (every day): According to the FBI, over 70% of ransomware victims are small and mid-sized businesses. Why? They often lack advanced defenses, making them easier targets. The message is clear: ransomware doesn’t discriminate . Whether you’re a manufacturer, professional services firm or municipality—if you use technology to run your business, you are at risk. How Humans Are Used to Execute Attacks Cybercriminals increasingly rely on human behavior to breach defenses: Phishing & Impersonation : Attackers impersonate employees and trick help desk staff into provisioning access. Groups like Scattered Spider use native English speakers to convincingly pose as internal staff. Credential Theft : Employees reuse passwords or fall for fake login pages. These credentials are sold on the dark web and used to infiltrate networks [1] . Employee Burnout : Tired or disengaged employees are more likely to click suspicious links or ignore security protocols. In one survey, 63% of employees admitted they’d open a suspicious email if it appeared to come from a colleague . Overconfidence : Despite training, many employees believe they can spot phishing—but attackers now use AI to craft flawless messages. “Human error is the biggest contributor to any data breach. Nearly three out of four incidents involved a human element like error, privilege misuse, stolen credentials or social engineering.” — Infosec Institute Ransomware Readiness Checklist Here’s a step-by-step framework to strengthen your defenses: Educate Your Team – Human error is still the #1 cause of successful ransomware infections. Regular phishing simulations and awareness training are critical. Teach staff to not click unverified links, avoid unknown USB devices and use VPNs on public networks. Patch and Update Systems – Cybercriminals exploit known vulnerabilities. Keep servers, applications and endpoints up to date. Use firewalls and endpoint protection. Segment Your Network – Don’t let attackers move freely inside your systems. Limit access and separate critical infrastructure from general-use networks. Secure Your Backups – Keep backups encrypted, offsite and inaccessible from the primary network. Test them regularly to confirm they can be restored. Implement Multi-Factor Authentication (MFA) – Passwords alone are not enough. Require MFA for remote access, admin accounts and email. Monitor and Respond 24/7 – Early detection is everything. Proactive monitoring tools can identify and lock down suspicious activity before it escalates. Keep systems updated, and watch for LOTL tactics, blind spots and unusual activity—especially during nights and weekends. Develop (and Test) a Response Plan – Conduct regular tabletop exercises. Know who to call, how to isolate infected systems and how to restore operations quickly. From Readiness to Resilience Cybersecurity isn’t about eliminating every risk—that’s impossible. It’s about building resilience so your business can withstand attacks and bounce back stronger. Seifert Technologies designs ransomware readiness and recovery strategies with the right combination of prevention, detection and recovery strategies. Don’t wait until you’re locked out. Let’s build your defense plan today. Contact us to schedule a free consultation. Call 330.833.2700 ext. 113 or email sales@seifert.com .

By Seifert Technologies
•
June 24, 2025
Backups protect your files. Disaster recovery protects your business. Most business owners understand the importance of backing up their data. Few realize that backups alone won’t protect them when disaster strikes. Relying solely on backups is one of the most common (and costly) mistakes business owners can make. If your organization hasn’t defined a full recovery plan, you could be at risk. Backup vs. Disaster Recovery: What's the Difference? Data Backup creates a copy of your files, folders and network systems. These backups can be stored locally or in the cloud, and they are meant to protect against data loss. Disaster Recovery (DR) is a comprehensive strategy outlining how to restore critical IT systems, applications, and operations after a major disruption. It defines key recovery processes, timelines, failover systems, resources and responsibilities. Having a backup is like having a spare tire; Disaster Recovery is having the right tools and knowing how to use them to get back on the road. Why Backups Alone Aren’t Enough Here are a few ways businesses get blindsided when they rely on backups alone: Restoration Takes Time: Just because files are saved doesn’t mean your system can be restored instantaneously. Restoring servers, reconfiguring networks and reinstalling applications can take days—or even weeks—without a recovery strategy. Lack of Prioritization: Not all data is equal. Without a recovery strategy, teams waste hours recovering low-priority files while other critical systems remain offline after a ransomware attack, server failure or natural disaster. Downtime Is Expensive: According to FEMA, 90% of small businesses fail within a year if they can’t reopen quickly after a disaster. Downtime can lead to thousands of dollars in lost revenue, damaged reputations, compliance violations and lost productivity. Cybercriminals Target Backups: Modern ransomware attacks often look for and encrypt backups first. If your backup isn’t isolated or secure, it could be compromised before you even know there’s a problem. What a Resilient Disaster Recovery Strategy Looks Like Build real-world resilience with a practical, right-sized recovery plan: Redundant, Automated Backups: Implement multi-layered backup strategies that include local and cloud storage, to ensure that even if one method fails, your data is still recoverable. Defined RTO and RPO Goals: Define Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) to determine how quickly your systems must be restored and how much data loss is acceptable. These benchmarks will guide the technology and processes used in your plan. Disaster Recovery Runbook: Outline the step-by-step process for restoring operations after a disaster. Include system dependencies, key personnel responsibilities and a communications strategy. Regular Testing and Validation: Conduct routine Disaster Recovery drills and simulations to ensure your systems and people are ready. Cloud-Based Recovery Options: For businesses that can’t afford extended downtimes, explore Disaster Recovery as a Service (DRaaS) options. This allows you to spin up virtual versions of critical systems from the cloud, often within hours or minutes, depending on business needs. Don’t Wait Until It’s Too Late Data loss, cyberattacks, power outages and hardware failures are not rare events—they’re part of an everyday business environment in our always-on, always-connected world. The companies that survive and thrive through these events are the ones that plan ahead. Disaster recovery isn’t just for large enterprises. Small and mid-sized businesses have the most to lose from prolonged downtime. The good news is that with the right IT partner, recovery is more accessible and affordable than ever. Let’s Build Resilience—Together At Seifert Technologies, we specialize in right-sized, strategic disaster recovery solutions for growing businesses. Whether you're starting from scratch or want a second opinion on your current backup strategy, we’re here to help. We’ll evaluate your setup, identify vulnerabilities and recommend a path toward true resilience. Contact us today to schedule a free consultation. Call 330.833.2700 ext. 113 or email sales@seifert.com .

By Seifert Technologies
•
April 24, 2025
AI isn’t just a buzzword anymore, and it’s not just for Fortune 500 companies. It’s quietly reshaping how businesses—especially small and mid-sized ones—manage their IT, protect their data, and improve productivity. Yet for many business owners, AI still feels like something out of reach. Maybe you’ve heard of ChatGPT or Microsoft Copilot, but you’re not quite sure how it fits into your world. That’s where we come in! We’re breaking down what AI means for your IT operations today—and how Managed IT Service Providers (MSPs) like us are helping businesses like yours get ahead without getting overwhelmed. What AI Is Doing for IT Management at SMBs (Right Now) From cybersecurity to automation, AI is already making IT faster, smarter, and more secure. Here’s how: 1. AI-Powered Cybersecurity AI tools are becoming essential to detect and stop threats to your business before they become disasters. 24/7 threat detection : Tools like SentinelOne and Microsoft Defender use AI to monitor your systems in real-time and spot suspicious activity—even before a human could. Phishing protection : AI analyzes emails and links to catch impersonation attempts and scam messages. Automated response : If a threat is detected, AI tools can automatically isolate infected systems and prevent spread—within seconds. This is key, pairing your 24/7/365 threat detection with 24/7/365 action! 2. Smarter IT Automation AI isn’t just about fighting cybercrime—it’s helping businesses save time, reduce manual work, and operate more efficiently. Here are some examples of how AI is automating key IT functions behind the scenes: Predictive maintenance : AI can flag hardware or software issues before they cause downtime. User behavior analysis for better permissions control : AI tools can monitor how employees use systems and flag risky access patterns—helping prevent accidental data exposure or insider threats. Intelligent alert prioritization: Instead of flooding your IT dashboard with noise, AI filters and ranks alerts by severity—so real issues don’t get buried under false positives. Self-healing systems : In some cases, AI can detect and fix common problems (like restarting a frozen service) without any human involvement. These aren’t hypothetical tools—they’re already in use by MSPs and IT platforms supporting businesses like yours every day. 3. Productivity Gains with Tools You Already Have If your business uses Microsoft 365, you already have access to AI—and probably aren’t using it fully yet. Microsoft Copilot (Word, Excel, Outlook, Teams): Draft emails, summarize meetings, or create reports with just a few clicks. Summarize long threads and documents Build presentations or clean up Excel data without formulas or formatting headaches. Outlook Suggestions : AI can suggest meeting times, draft responses, or flag important messages. Teams AI features: Transcripts, highlights, and action items from meetings—delivered directly after the call. These tools don’t require a tech degree to use—they just need someone to turn them on, configure them properly, and show you how to use them. That’s where we come in. Our job is to make it easy, secure, and practical for you so you can focus on what you know best…your business. Why Business Owners Shouldn’t Wait AI isn’t going away. And for businesses that get ahead of it, there’s a real opportunity to: Outpace competitors with faster decisions and smarter tools Protect against modern cyber threats Reduce costs through automation and efficiency Empower employees with tools that make work easier, not harder The good news? You don’t need a full-time IT team or a PhD in machine learning. You just need the right partner to guide you. Let’s Talk About AI for Your Business Curious about what AI could do for your business? Overwhelmed by options and don’t know where to start? Let’s fix that. Schedule a call with our team to discuss your business, your systems, and where AI could make the biggest difference—today and in the future.








